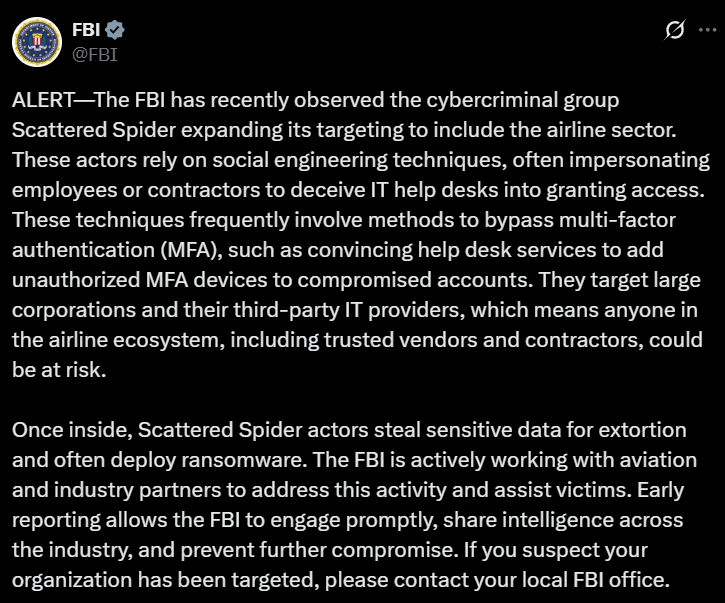
The FBI has issued a new warning that the cybercriminal group known as Scattered Spider is now targeting the airline industry, expanding its campaign of social engineering, data theft, and ransomware against critical infrastructure.
Previously known for infiltrating major corporate networks through impersonation and phishing tactics, Scattered Spider has recently shifted its focus to the aviation sector, including airlines, contractors, and third-party IT vendors, according to the FBI.
How They Operate
Scattered Spider—also known as UNC3944, Starfraud, Muddled Libra, and Scatter Swine—relies heavily on social engineering techniques to gain access. They frequently impersonate employees or IT staff to trick help desks into granting access to systems or registering unauthorized multi-factor authentication (MFA) devices. Their tactics are specifically designed to bypass MFA protections, making even secured accounts vulnerable.
Once inside, the group exfiltrates sensitive data, extorts organizations, and in many cases, deploys ransomware—particularly the BlackCat/ALPHV variant. Their attacks often begin with phishing or smishing attempts and escalate to SIM-swapping and impersonation-based account takeovers. The FBI has also reported the use of legitimate remote access tools like TeamViewer, Ngrok, and Mimikatz, making detection more difficult.
Why Airlines Are at Risk
The airline industry is uniquely vulnerable due to its complex network of employees, vendors, and contractors—many of whom rely on remote access and federated identity systems for operational efficiency. This ecosystem creates multiple entry points for attackers. The FBI stresses that any organization connected to an airline’s IT infrastructure could be a potential target.
“These actors rely on social engineering techniques, often impersonating employees or contractors to deceive IT help desks into granting access. These techniques frequently involve methods to bypass multi-factor authentication (MFA), such as convincing help desk services to add unauthorized MFA devices to compromised accounts.,” the FBI noted.
Previous Warnings and Tactics
This escalation follows a 2023 joint advisory from the FBI and CISA (Cybersecurity and Infrastructure Security Agency), which outlined the group’s detailed tactics, techniques, and procedures (TTPs). That advisory (AA23-320A) highlighted their ability to exploit MFA weaknesses, escalate privileges via identity provider tampering, and maintain persistence using legitimate tools like Splashtop and Pulseway.
The group has also been observed monitoring internal communications like Slack and Teams to stay ahead of incident response efforts, and even joining live security calls under false identities.
What Organizations Can Do
The FBI and CISA recommend the following immediate actions:
- Enforce phishing-resistant MFA, such as FIDO2 or PKI-based solutions.
- Audit help desk processes to prevent unauthorized changes to authentication methods.
- Segment networks and limit administrative privileges.
- Regularly patch systems and conduct simulated phishing awareness training.
- Monitor for abnormal remote access activity and implement allowlisting for software execution.
Organizations should report suspicious activity to their local FBI office or CISA’s 24/7 Operations Center.
Contact and Resources
If your organization suspects a breach, contact:
- FBI Field Office: www.fbi.gov/contact-us/field-offices
- CISA 24/7 Center: [email protected] or 888-282-0870
For more information:
The FBI underscores the importance of early reporting, which enables them to share indicators of compromise across industries, limiting the impact of these increasingly aggressive cyberattacks.
Feeling lost in the digital world? Dr. Tom is here to help!
Join Dr. Tom every week in his column, Dr. Tom’s Cyber Bits and Tips, for byte-sized advice on all things cyber and tech. Whether you’re concerned about online safety, curious about the latest cybercrime trends, or simply want to navigate the ever-evolving digital landscape, Dr. Tom has you covered.
From practical cybersecurity tips to insightful breakdowns of current threats, Dr. Tom’s column empowers you to stay informed and protect yourself online. So, dive in and get savvy with the web – with Dr. Tom as your guide!
Sign up for our Sunday Spectator. Delivered to your inbox every Sunday, with all the news from the week.