Your IP address is your digital fingerprint—it’s how websites, services, and third parties identify and communicate with your device on the internet. But this unique identifier can also expose your location, browsing history, and even your identity. For privacy-conscious users, journalists, remote workers, or anyone seeking more control over their digital footprint, understanding how to conceal your IP address is essential.
Let’s dive deeper into three powerful tools that help you stay safe, anonymous, and secure online: Virtual Private Networks (VPNs), The Onion Router (TOR), and proxy servers.
1. Virtual Private Network (VPN): Secure, Encrypted, and Versatile
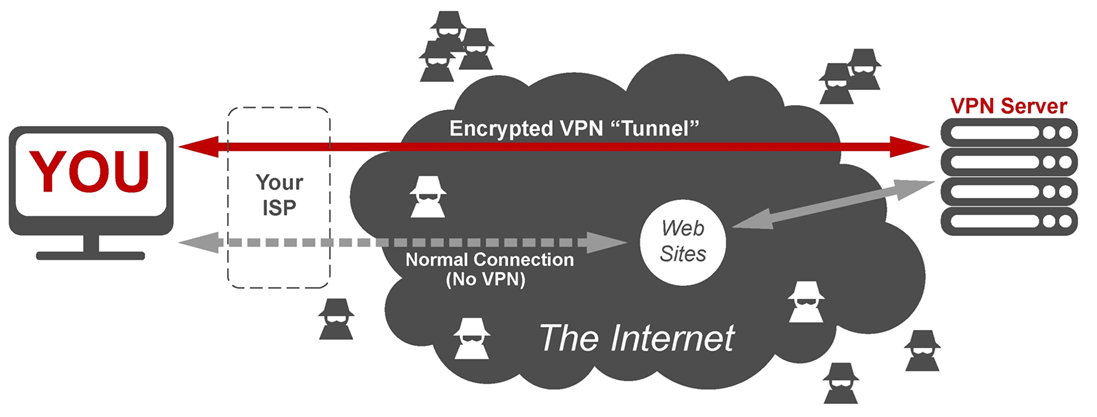
A VPN (Virtual Private Network) creates a secure, encrypted tunnel between your device and a remote VPN server. All your internet traffic is routed through this tunnel, which means that your ISP, hackers, or third-party trackers can’t see what you’re doing online. Only the VPN server sees your actual IP address—everyone else sees the VPN’s. An VPN is a full software package you will install on your computer. After installation, you launch the VPN software and connect to one of their servers. Once connected, all your Internet traffic is encrypted and routed through the VPN server. Many VPNs are also have applications for your cell phone, so you can protect your traffic and stay anonymous on your phone as well.
🔐 Key Benefits:
-
IP Address Masking: Your real IP address is hidden and replaced with that of the VPN server. This makes your location appear to be wherever the VPN server is based, which is useful for accessing geographically restricted content.
-
Data Encryption: VPNs encrypt your data before it leaves your device. Even if someone intercepts your traffic—like on public Wi-Fi—they won’t be able to read it.
-
Bypass Censorship and Geo-blocking: VPNs allow users to access content that’s restricted in certain regions. For example, you can watch Netflix U.S. content while traveling abroad.
-
Work-from-Home Security: VPNs offer businesses a secure way for remote employees to access internal systems without leasing expensive private lines.
🧠 Things to Know:
-
VPNs are available as apps for desktops, smartphones, and tablets.
-
Paid VPNs (e.g., ProtonVPN, PIA, NordVPN) are generally more trustworthy and don’t log your activity.
-
Free VPNs may track and sell your data—defeating the point of using one. Although Proton VPN offers a free service that I highly recommend.
A VPN is one of the best all-around tools for protecting your identity, especially for everyday use, online banking, streaming, and secure browsing.
2. TOR (The Onion Router): Powerful Anonymity for Sensitive Tasks
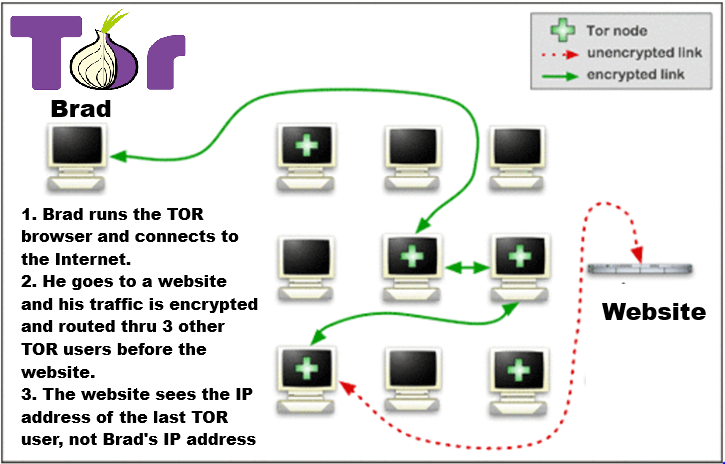
TOR is a decentralized anonymity network that uses a system of volunteer-operated relays (nodes) to route your internet traffic through multiple layers of encryption. Each relay only knows the IP address of the previous and next hop, not the full path. This makes it incredibly difficult to trace your activity back to your original IP. The easiest way to use TOR is to download the TOR browser to your computer. The TOR browser is a stand alone application, and when you launch it, a new Internet browser opens on your computer. Everything you do inside of that browser is protected and anonymous. Applications and traffic outside of the TOR browser, ie the rest of your computer is not protected. TOR is also available for Android phones.
🧅 How It Works:
-
Your traffic is encrypted multiple times and passed through a random chain of nodes.
-
Each node peels away a single layer of encryption (like an onion) and passes it to the next.
-
The final node, the exit node, decrypts the last layer and sends the data to the destination website.
🕵️ Best Use Cases:
-
High-stakes privacy: Ideal for whistleblowers, journalists, and activists in oppressive regimes.
-
Accessing .onion websites: These hidden services are only accessible via TOR and include forums, messaging platforms, and research tools.
-
Preventing traffic analysis: TOR hides not only your destination but also your browsing patterns.
⚠️ Considerations:
-
Slower speeds due to traffic bouncing across multiple nodes.
-
The exit node can see your unencrypted traffic, so avoid transmitting sensitive data without HTTPS.
-
Not ideal for casual use—logging into personal accounts like Facebook defeats the purpose of anonymity.
While TOR offers exceptional privacy, it’s best suited for situations where anonymity is more important than speed or convenience.
The TOR Browser can be download at https://www.torproject.org/
3. Proxy Servers: Simple, Fast, and Good for Basic Anonymity
A proxy server is a middleman between your device and the internet. There are two types of proxies, a client and a web proxy. We will only cover the web proxy here. When you connect to a website using a proxy, the proxy server makes the request on your behalf. The website only sees the proxy’s IP address, not yours. With a web proxy, you go to the web proxy site and enter the website you want to view in the web proxy site. The web proxy then shows you the website, inside their website.
🔄 How It Works:
-
You connect to the proxy server.
-
The proxy server forwards your request to the target website.
-
The website sends its response back to the proxy, which then passes it along to you.
📈 Benefits:
-
IP Obfuscation: Hides your real IP address, allowing for anonymous browsing.
-
Web Filtering and Logging: Companies often use proxies to block websites or track employee internet usage.
-
Faster Access via Caching: Frequently visited websites can be stored (cached) by the proxy, allowing for quicker load times and reduced bandwidth.
🚫 Limitations:
-
No encryption: Unlike VPNs or TOR, most proxies do not encrypt your traffic, leaving it vulnerable to interception.
-
Limited scope: Proxies typically work on a per-application basis (like just your browser), while VPNs route all device traffic.
-
Logging risks: Some public proxy services may log your activity and sell the data to advertisers or worse.
Use proxy servers when you need quick, simple anonymity, such as bypassing IP-based access blocks, but avoid using them for secure activities like online banking or transferring sensitive files. A few proxy websites to try, https://proxysite.com, https://kproxy.com, and https://croxyproxy.com.
🧠 Final Thoughts: Choosing the Right Tool
| Tool | Best For | Pros | Cons |
|---|---|---|---|
| VPN | Everyday secure browsing, public Wi-Fi, geo-unblocking | Encrypts data, hides IP, full-device coverage | May cost money, trust depends on provider |
| TOR | Maximum anonymity, whistleblowing, accessing dark web | Multi-layer encryption, hard to trace | Slow speeds, not ideal for casual browsing |
| Proxy Server | Basic anonymity, bypassing IP blocks | Fast, easy, cached content | No encryption, limited to apps or browsers |
For the best protection, consider combining tools (e.g., using TOR with a VPN, which Proton VPN supports). But no tool is perfect—your overall security also depends on safe online habits, updated software, and a good understanding of risks.
Feeling lost in the digital world? Dr. Tom is here to help!
Join Dr. Tom every week in his award winning column, Dr. Tom’s Cyber Bits and Tips, for byte-sized advice on all things cyber and tech. Whether you’re concerned about online safety, curious about the latest cybercrime trends, or simply want to navigate the ever-evolving digital landscape, Dr. Tom has you covered.
From practical cybersecurity tips to insightful breakdowns of current threats, Dr. Tom’s column empowers you to stay informed and protect yourself online. So, dive in and get savvy with the web – with Dr. Tom as your guide!
Sign up for our Sunday Spectator. Delivered to your inbox every Sunday, with all the news from the week.